Hi, we're planning to use your SSO to be integrated with our own registration and login system. I have a ques: how do we actually login to crowdstack from our site with the use of SSO? I checked your API calls and can see that you have endpoints for SSO member lookup as well as the login endpoint however, in your login, we need to provide the password which we don't have since we're just logging in from our site. Please let me know what do we need to do or use to achieve this. Thanks.
Replies sorted oldest to newest
Hi @Harvey Mercado,
The API is not meant to be used for Single Sign-On; rather it's more of a tool for pushing and pulling data to/from Crowdstack programmatically.
Crowdstack uses SAML 2.0 for SSO, so in order to hook up your Crowdstack via SSO, you will need to implement a SAML Identity Provider on your registration and login system. In SSO mode, Crowdstack will act as a SAML Service Provider.
SAML 2.0 is an open standard with tons of information widely available. You can learn more about SAML 2.0 here:
You can also probably find a SAML SDK to ease your implementation. For example, OpenSAML is a C++ and Java SDK.
Note that Crowdstack uses SAML's HTTP POST binding, so you'll want to make sure you support that in your implementation.
Once you have your SAML Identity Provider in place on your website, you can share the SAML metadata XML to start the SSO configuration process in your Crowdstack control panel under Settings -> Single Sign-On.
The SAML metadata for your Crowdstack Service Provider can be found at the /saml/metadata path, relative to your Crowdstack domain.
Let us know if you have any questions about this!
Regards,
Brian
Thanks for your reply, appreciate your prompt response. I will check out OpenSAML for the implementation.
Actually, the goal is for the users in our website to access pages in crowdstack without having to do any additional registration with crowdstack. Do we need a crowdstack account for this? After we set up SAML identity provider in our website as well as, configure SSO and upload the metadata in crowdstack. How do we log in (or register, for new users) to crowdstack from our website? Do you have sample implementation that we can look into?
Thanks again.
Hi @Harvey Mercado,
You can set up your SSO configuration so that users of your system will be automatically registered in Crowdstack without any further registration steps. To do that, you need to make sure that your SAML Assertion provides all of the profile fields for Crowdstack, which includes, at a minimum, Email Address and Display Name.
Once you have everything set up, then anyone who visits Crowdstack will need to sign in or register on your external system in order to get signed in within Crowdstack.
We don't have a sample implementation to provide, unfortunately.
Hope this helps!
Brian
Thanks for all the help. I really appreciate it.
We're currently setting up IdP SAML SSO on our side. Btw, what do we need to enter as destination url when sending request to crowdstack?
Also, do we need to set the issuer, audience restriction, etc. in crowdstack as well? I have found a sample implementation on OpenSAML IdP-initiated SSO for Okta that I'm currently using as reference and its using issuer, destinationUrl, audienceRestriction, etc. along with the keystore for signing.
I checked SSO topic in crowdstack and it doesn't say much on how it is configured in crowdstack as the SP except for just uploading the metadata, I was wondering if you have other links for crowdstack documentation on SSO which has additional information.
Hi @Harvey Mercado,
What Destination URL are you referring to? Are you referring to the SAML Assertion? If so, Crowdstack doesn't use Destination URL.
Note that the Assertion Consumer Service URL is defined in your Crowdstack SAML metadata, which is found at the /saml/metadata path in Crowdstack. I don't know which Crowdstack you're affiliated with or I would provide the direct URL to you.
Crowdstack doesn't put any requirements on the Issuer or Audience. You will need to make sure the Request ID is properly returned per the SAML Assertion standard.
The only other real requirement is to use the HTTP POST binding, as reflected in Crowdstack's SAML metadata. You can pass Email Address and Display Name as attributes in the Assertion, as well as other profile fields. You'll have the ability to configure these once you have your IdP set up and load your metadata XML into the Crowdstack control panel.
I would recommend you don't worry too much about those specifics and get to where you have a functional IdP that implements SAML standards, get your metadata uploaded to Crowdstack, and then take a look at the configuration from there.
If you have any questions or issues during integration, just let us know if we can assist.
Regards,
Brian
Thanks for the reply. I have already the initial code implementation with SAML standard using OpenSAML. However, I'm still figuring out how to generate/build the xml metadata to be uploaded to Crowdstack. Do you have any idea on this?
Thanks Brian.
This is the crowdstack account where we would like to setup the SSO: Home | Manchester Unity (crowdstack.io)
I was checking it out and wondering where I could get the Crowdstack SAML metadata and find the ACS Url as mentioned in your last reply. Can you please help where I could find this file and url?
Also, where can I see the Request ID that is to be returned? Is this the ID in the SAML Response like the one highlighted below?
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="_8e8dc5f69a98cc4c1ff3427e5ce34606fd672f91e6" Version="2.0" IssueInstreply. Can you pleaant="2014-07-17T01:01:48Z" Destination="http://sp.example.com/demo1/index.php?acs" InResponseTo="ONELOGIN_4fee3b046395c4e751011e97f8900b5273d56685">Best Regards
Hi @Harvey Mercado,
You can find the Crowdstack SP SAML metadata here:
https://manchesterunity.crowdstack.io/saml/metadata
Since Crowdstack will be performing the AuthnRequests, Crowdstack will define the Request ID. You just have to make sure you match your Assertion response to the Request ID it corresponds to.
Hope this helps!
Brian
Got it. Thanks so much for all your help.
One more thing while I'm trying to write the xml metadata by hand and looking at the EntityId which is by default, points to localhost:9443, should I need to use/install a separate Identity Server like WSO2? I'm currently using OpenSaml 3.0 to build the assertion with the AuthnRequest which btw you mentioned, should come from Crowdstack's side so that makes me wonder if I need both the identity server like WSO2 and OpenSaml or should I only need one of these to configure SSO with Crowdstack.
Hi @Harvey Mercado,
I'm not familiar with WSO2 or how it might interoperate (or not) with OpenSAML, so I don't think I can advise you on that.
The basic flow is that Crowdstack will send an AuthnRequest POST to your IdP, and your IdP will need to handle the user's login (if necessary) and send a SAML Assertion POST back to Crowdstack. In order for this to work, of course, you'll need your SAML IdP to be hosted somewhere on the Internet over HTTPS. localhost won't be a viable option, of course.
Sorry I can't be of more help with the specific tools you're using!
Brian
Thanks for your prompt reply. I think what you're referring to is when a user logs in to Crowdstack and to redirect this user to us for authentication. But what about if the user logs in to our site and we want it to automatically log in to Crowdstack and probably bring out a page on our site. Do we send an AuthnRequest for that? Is the possible?
One other thing that I'd like to clarify regarding the basic flow you mentioned above, where is Crowdstack going to send the AuthnRequest? where do we read it?
Hi @Harvey Mercado,
You won't be able to do an IdP-initiated login request, which is what you're asking for. I wouldn't worry about this auto-sign in scenario just yet. I'd focus first on the basics of getting the SAML IdP AuthnRequest processing and Assertion response working. Get that set up and working. Then, you can start looking at how to handle automatic logins. When you get there, you'll have a couple of options:
- Probably the best option is to enable "Auto Sign-In Mode" in Crowdstack. What this will do is cause Crowdstack to automatically send users through your IdP any time they establish a new session on Crowdstack. This way, you don't have to do anything special on your end when the user signs in.
- An alternative, if you really want to establish a session in Crowdstack immediately when a user signs in to your system, is to redirect to Crowdstack's
/loginURL, which will trigger the SAML AuthnRequest implicitly. That URL also supports aredirectquery parameter which you can use to define where the user should go on completion of the login (e.g. if you want them to return back to your site).
Again, though, I wouldn't worry about auto-login until you have the basic SSO integration hooked up and working. If you take this kind of incremental approach to developing the integration, I think it'll go smoother for you.
Hope this helps!
Brian
Hi @Brian Lenz,
First of all, I'd like to thank you for all your help. Much appreciated.
I uploaded a metadata xml to crowdstack and clicked on Submit to update the settings I have entered.
However, I can longer access crowdstack's metadata using the following url: https://manchesterunity.crowdstack.io/saml/metadata
Can anybody help me check on this?
Thanks and best regards,
Harvey
Hi @Harvey Mercado,
It looks like your SAML IdP doesn't support signing? You'll need to enable that in order to ensure the integrity and authenticity of requests from your IdP. Once you've enabled signing, your SAML metadata should include the signing certificate. Once you have the new SAML IdP metadata XML with the signing certificate included, then go back into your control panel:
https://manchesterunity.crowdstack.io/cp/sso-settings
And click the link to Re-import SAML IdP Metadata XML. Upload the SAML metadata XML, and that should correct the problem.
We'll see about improving the user experience in this scenario to make the issue more apparent.
Hope this helps!
Brian
Hello,
Below is part of the xml that I have uploaded where I think it already covers the certificate for the signing? Btw, I'm using SSOCircle as public IDP where I got this metadata and I have configured our application as SP to talk to this same public IDP account for the SSO.

Still figuring out what else have gone wrong. I greatly appreciate your prompt response despite the holidays.
Best Regards,
Harvey
Attachments
Hi @Harvey Mercado,
Can you upload the SAML metadata XML here so I can take a look at it? It looks like Crowdstack isn't able to extract the signing certificate for some reason, so if I can take a look, I should be able to assist further.
Thanks,
Brian
Hi @Brian Lenz,
Please see attached xml metadata that was also uploaded in crowdstack for this account.
Best Regards,
Harvey
Attachments
Hi @Harvey Mercado,
Sorry for the delay in getting back to you. Happy New Year 
My guess is that the formatting of your X509Certificate elements is the problem. It looks like you have them formatted with spaces between the lines, but those should actually be newlines. Aside from the newlines, there should not be any other whitespace in the elements (no leading whitespace and no trailing whitespace, either). That's my best guess as to what is throwing things off.
Try fixing that and see if it makes a difference?
Brian
Thanks and Happy New Year @Brian Lenz.
I did try and update the metadata according to your instructions, however, the issue still exists.
I reset the settings then I realized that the issue only exists if I tick the checkbox for enabling the SSO as shown in the screenshot below: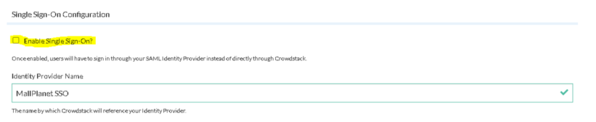
Not sure how to proceed with this. Do you know how do I address this? Please let me know.
I also need to upload crowdstack's metadata xml from (https://manchesterunity.crowdstack.io/saml/metadata) to ssocircle as the IdP but its asking for the FQDN as shown below. Would you happen to know where I can get it? I initially entered "manchesterunity.crowdstack.io" as FQDN. Would this be okay?
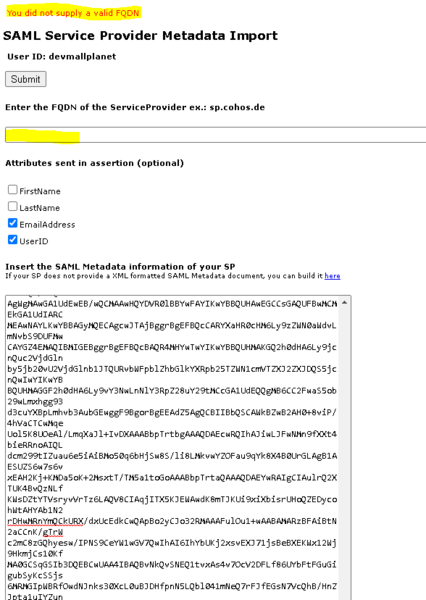
Attachments
Hi @Harvey Mercado,
OK, I've fully diagnosed what's going on here now. It turns out the spaces / formatting of the certificate is not the issue. Your IDPSSODescriptor has WantAuthnRequestsSigned="false", which is causing Crowdstack to ignore the signing certificate. Then, there is a bug in Crowdstack that is preventing its SAML SP from working properly due to the signing certificate being unspecified, which is the root cause of the errors you're experiencing. We are working on a fix for that issue at the moment.
You have two options:
- Change your IdP to want signed Authn requests (
WantAuthnRequestsSigned="true") and re-import the metadata XML into Crowdstack. - Wait until we get a bug fix deployed, which should be some time in the next couple of hours. Once the bug fix is deployed, your current scenario / configuration should work without incident.
Hope this helps! If you have further questions or issues, let me know ![]()
Brian
Hi @Harvey Mercado,
The bug fix has been deployed, and the Crowdstack SAML SP metadata XML is now working without issue:
https://manchesterunity.crowdstack.io/saml/metadata
Regards,
Brian
@Brian Lenz Thanks so much for all your help.
But what if I want to change the IDP I set up earlier. I can no longer access the Settings page for me to upload another metadata xml.
I set up single sign on earlier however, I got an error after logging to the idp, please see screenshot below:

So I'm exploring other options and I have another metadata xml that I would like to upload but I couldn't get to the page because of the error above. Appreciate all your patience and help in all these.
Attachments
Hi @Harvey Mercado,
There's a "backdoor" login form that you can use to sign in as an administrator to your Crowdstack:
https://manchesterunity.crowds...n?showLoginForm=true
You should be able to sign in there with your original Crowdstack email address and password, which should allow you in to the control panel to make further changes to your SSO integration.
Hope that helps!
Brian
Thanks @Brian Lenz.
One more thing, I am trying to upload a new metadata however, I'm getting the error below saying its invalid but cut short of telling me what exactly is invalid with this file and how to address it.
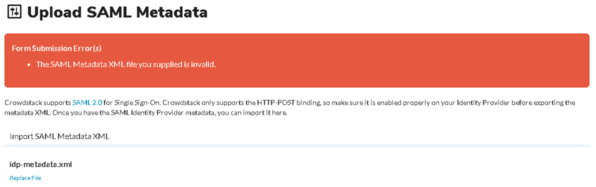
I have attached the new metadata file here, in case you have the chance to check it out.
Thanks again.
Attachments
Hi @Harvey Mercado,
The issue is that you have duplicate signing keys specified in the XML. You'll need to remove one of them, as it's not valid to have multiple signing keys.
Hope this helps!
Brian